Kubernetes Best Practices to Know
Kubernetes is a powerful container orchestration platform that helps automate the deployment, scaling, and management of containerized applications. To ensure smooth operation and optimize your Kubernetes deployments, it’s essential to follow best practices.
Read Also – How to install Kubernetes with Kubeadm
Here are some Kubernetes best practices along with examples and images to illustrate them:
- Use Declarative Object Configuration:
Instead of making manual changes to the cluster, define the desired state using declarative YAML or JSON configuration files. For example, here’s a YAML configuration file for a Deployment that creates three replicas of an application:
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-app-deployment
spec:
replicas: 3
selector:
matchLabels:
app: my-app
template:
metadata:
labels:
app: my-app
spec:
containers:
- name: my-app-container
image: my-app-image:latest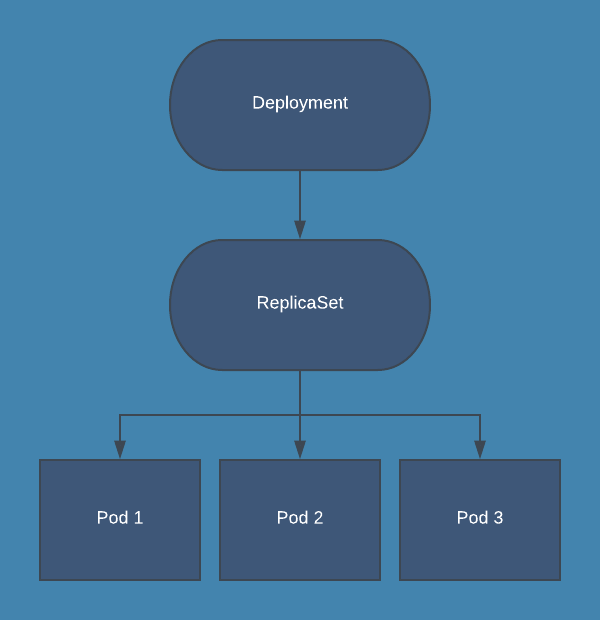
- Implement RBAC (Role-Based Access Control):
Use RBAC to control access to your Kubernetes cluster. Define roles and permissions to restrict access based on user roles and responsibilities. For example, here’s an example of defining a role and role binding in a YAML configuration file:
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: my-role
namespace: my-namespace
rules:
- apiGroups: [""]
resources: ["pods", "services"]
verbs: ["get", "list", "create", "update", "delete"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: my-role-binding
namespace: my-namespace
subjects:
- kind: User
name: john@example.com
roleRef:
kind: Role
name: my-role
apiGroup: rbac.authorization.k8s.io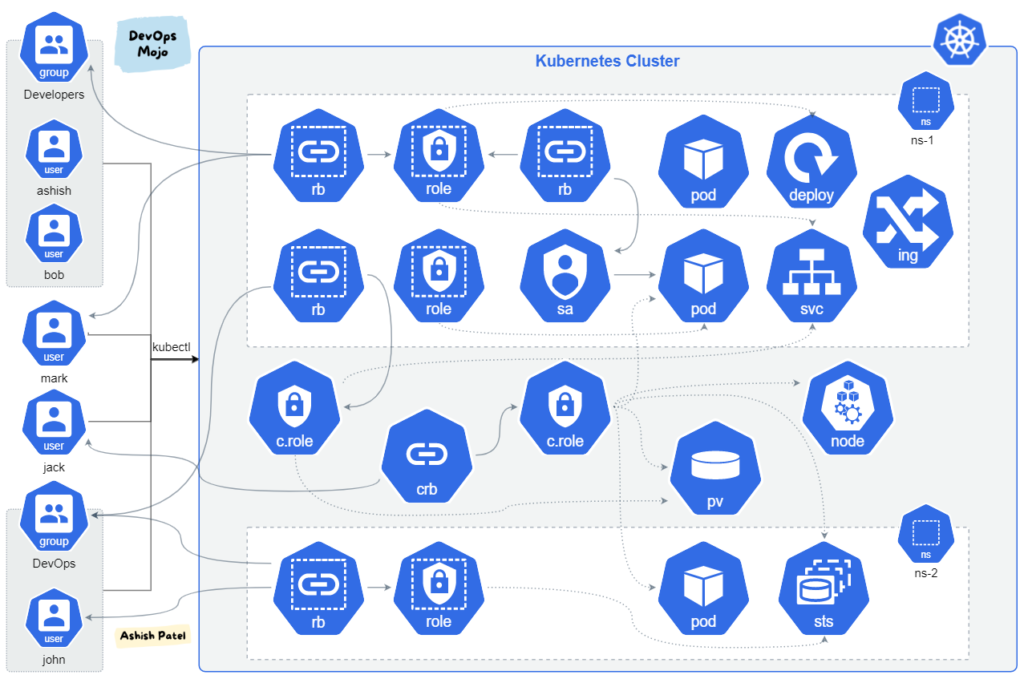
- Utilize Namespaces Effectively:
Create separate namespaces for different environments or projects. For example, you can create namespaces for development, staging, and production environments. Here’s an example of creating a namespace using thekubectl create namespacecommand:
kubectl create namespace development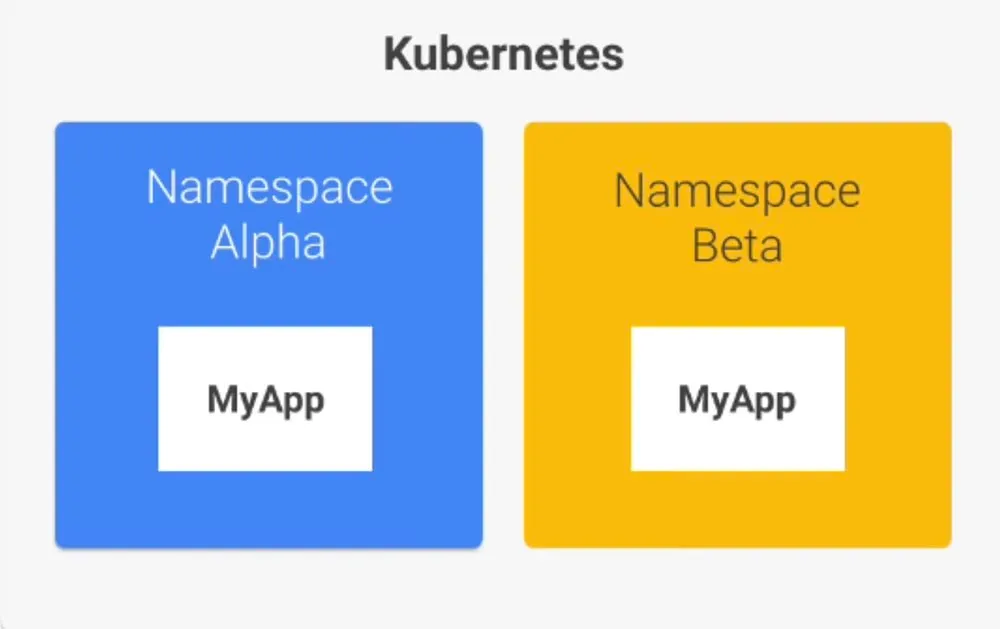
- Implement Network Policies:
Use Kubernetes network policies to define rules for network traffic within your cluster. This helps control communication between pods and services. Here’s an example of a network policy that allows traffic only from pods labeled withapp: my-app:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
spec:
podSelector:
matchLabels:
app: my-app
ingress:
- from:
- podSelector: {}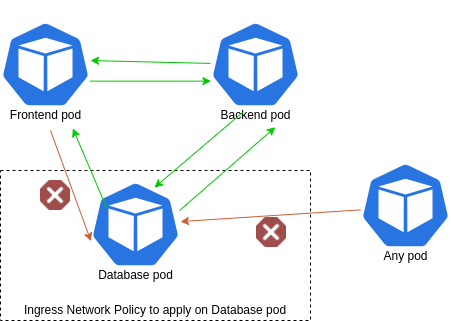
- Implement Pod Disruption Budgets (PDB):
Define Pod Disruption Budgets to control the number of pods that can be evicted simultaneously during disruptions. This ensures application availability during updates. Here’s an example of a PDB that allows at least two replicas of a Deployment to be available:
apiVersion: policy/v1
Latest posts by Mahesh Wabale (see all)
- Grafana Setup - June 30, 2025
- What is Grafana? - June 30, 2025
- Deploy Apache Tomcat Using Ansible - June 30, 2025

