
What is DevSecOps?
Modern enterprises are leveraging the collaborative approach of DevOps to automate rapid & reliable product delivery.
But what about security?
The goal is to implement checks on the same scale as app development. This approach eliminates the possibility of a threat at a later stage which would otherwise call for reworking countless lines of code – a tedious, time-consuming, and labor-intensive task!
Enterprises adopt this strategy because:
- Security is built into the product; not treated as an afterthought
- It ensures transparent workflows & timely collaboration during the development
- It facilitates faster recovery in case a threat is detected
Why DevSecOps Should be Your Top Priority?
Any lapse in security measures can invite a major loss of revenue & reputation. The risks of relaxed patches are immediate and expensive. It was also imposed with hefty fines due to a safety breach that exposed the data of their 50 million guests. No kidding, but you see their brand reputation took a huge blow!
Benefits of DevSecOps
- Issues can be identified & resolved much faster in the early stages of the SDLC (Software Development Life Cycle)
- Helps ensure and maintain compliance in the CICD pipeline from day one
- Offers more agility and pace to the assigned teams
- Automates securing of code to reduce vulnerabilities in apps while enabling predictable processes.
- Enables security professionals to focus their efforts and attention on remediating threats and eliminating the risk
- Enhances trust and transparency between teams right from the start
- Increases the delivery rate and reduces costs
- Facilitates consistent security with automation tools for testing and reporting
- Creates an immutable environment that takes up lesser hands-on time for account management, event monitoring, assessing vulnerability, code security & deploying checks.
Read Also – How to Setup Jenkins Master and Slave on Ubuntu 18.04 LTS
Key Components of DevSecOps Strategy:
1. Analyze Code
Identify vulnerabilities on time with the delivery of code in small, manageable chunks.
2. Manage Changes
Submit changes that can accelerate development speed and efficiency. Also, determine if the outcome of change is favorable or not.
3. Track Compliance
Ensure compliance with all applicable regulations including Payment Card Industry Digital Security Standard (PCI DSS) & General Data Protection Regulation (GDPR) and always be prepared for regulatory audits.
4. Detect Potential Threats
Every code update accompanies impending threats. It is vital to uncover these threats at the earliest and respond promptly.
5. Assess Vulnerability
Systematically review all weaknesses that can leave the system vulnerable. Define and delegate security levels to known weak points and recommend corrective action as and when needed.
6. Train Your Team
Involve your development and IT-ops teams in security-related training and equip them with the standard operating guidelines for set workflows.
DevSecOps Use Cases
Automated Testing
- Identifying potential issues before the testing kickstarts
- Automated management of security issues detected in real-time during the testing process
- Resolution of issues identified during development, deployment & testing
- Auditing & documentation of issues
- Monitoring and management of testing & quality checks
- Enhanced development awareness & improved collaboration
- Consistent configurations across all environments
- Simulated testing driven by artificial intelligence
Process Optimization
- Adjusting change management procedures for moving apps from Development to Testing to Production environments based on historical data
- Smart and effective management of code freeze & un-freeze
- Optimizing the SDLC based on data obtained from the delivery history of prior projects
- Prioritizing response and assigning alerts to the concerned teams based on past data
- Automated compliance checks across apps, integrations, and environments
Automating CI/CD Workflows
- Collating data on the success or failure of the build and assigning automated alerts
- Orchestrating complicated pipelines
- Automated segmentation & root cause analysis of deployment data
- Flagging potential problem areas for future builds using predictive analytics
- Assigning bug fixes and management of issues to the right people, based on design and deploy data from past projects
- Embedding security testing across the DevOps lifecycle
- Optimizing and implementing “Infrastructure as code” culture
Enhanced Collaboration
- Proactively identifying the potential to facilitate continuous feedback loops
- Making recommendations to address security issues promptly
- Enabling real-time collaboration between the development, security & operations teams
- Automated posting of problems and tagging different teams in collaboration tools
- Analyzing data streams generated from various heterogeneous tools and systems to establish correlations and achieve a holistic view of new deployments, production problems, and the app’s health
What is SAST SCAN ?
Static application security testing:
Scrubbing source code to identify and eliminate security vulnerabilities is known as static application security testing (SAST). Companies conduct the white box security testing practice in the early stages of the software development lifecycle. It is also often rerun at various intervals or when adds or changes are required.
Tailor-made for automation as DevSecOps products, SAST tools sift through code line by line to identify weak areas that can be bolstered to protect against known exploits. While this type of security scanning only detects what many consider low-hanging-fruit vulnerabilities, the automated tools are easy to run and interpret.
One of the major drawbacks to automated SAST tools is false positives. The tool does not have the intelligence required to analyze code that is in early stages and that cannot be compiled. However, baking greater levels of AI into these tools has shown to reduce false-positive events.
OWASP provides a list and breakdown of open source, free and commercial SAST tools. Popular open source options that can be added to your integrated development environment include the following:
- Bandit
- Flawfinder
- GitHub Advanced Security
- OWASP Automated Software Security Toolkit
What is DAST SCAN ?
Dynamic application security testing
While SAST looks at source code from the inside, dynamic application security testing (DAST) approaches security from the outside. A black box security testing practice, DAST tools identify network, system and OS vulnerabilities throughout a corporate infrastructure.
Because DAST requires applications be fully compiled and operational, run tests inside test/dev environments prior to production. Set up tools with preconfigured testing parameters, and automatically initiate multiple crawling activities and associated penetration tests to detect vulnerabilities. This reduces the risk of putting potentially vulnerable software in the hands of business users.
A drawback is DAST tools may not reach wide enough to test the entire attack surface, leading to some missed vulnerabilities.
OWASP provides a list of open source and commercial DAST tools. Popular open source options include the following:
- Deepfence ThreatMapper
- Nikto
- OpenVAS
- OWASP Zed Attack Proxy
Which Application you can use for implementing devsecops:
- Dependency Track
- Anchore
- Vault
- SonarQube
- Nexus Firewall
- Syft and Grype
Dependency Track:

Dependency-Track is an intelligent Component Analysis platform that allows organizations to identify and reduce risk in the software supply chain. Dependency-Track takes a unique and highly beneficial approach by leveraging the capabilities of Software Bill of Materials (SBOM). This approach provides capabilities that traditional Software Composition Analysis (SCA) solutions cannot achieve.
Dependency-Track monitors component usage across all versions of every application in its portfolio in order to proactively identify risk across an organization. The platform has an API-first design and is ideal for use in CI/CD environment
Anchore:

The vulnerability feed that provides data to v0.9 and earlier will be deactivated on June 30th 2022. Please ensure you have upgraded to 1.0 with the Grype-based provider enabled before this date to ensure you continue to receive updated vulnerability data.
For users interested in a supported commercial solution, schedule a demo to see Anchore Enterprise’s broad set of enterprise capabilities including SBOM management, security scanning, and reporting.
Vault:

Vault is a tool for securely accessing secrets. A secret is anything that you want to tightly control access to, such as API keys, passwords, certificates, and more. Vault provides a unified interface to any secret, while providing tight access control and recording a detailed audit log.
A modern system requires access to a multitude of secrets: database credentials, API keys for external services, credentials for service-oriented architecture communication, etc. Understanding who is accessing what secrets is already very difficult and platform-specific. Adding on key rolling, secure storage, and detailed audit logs is almost impossible without a custom solution.
SonarQube:
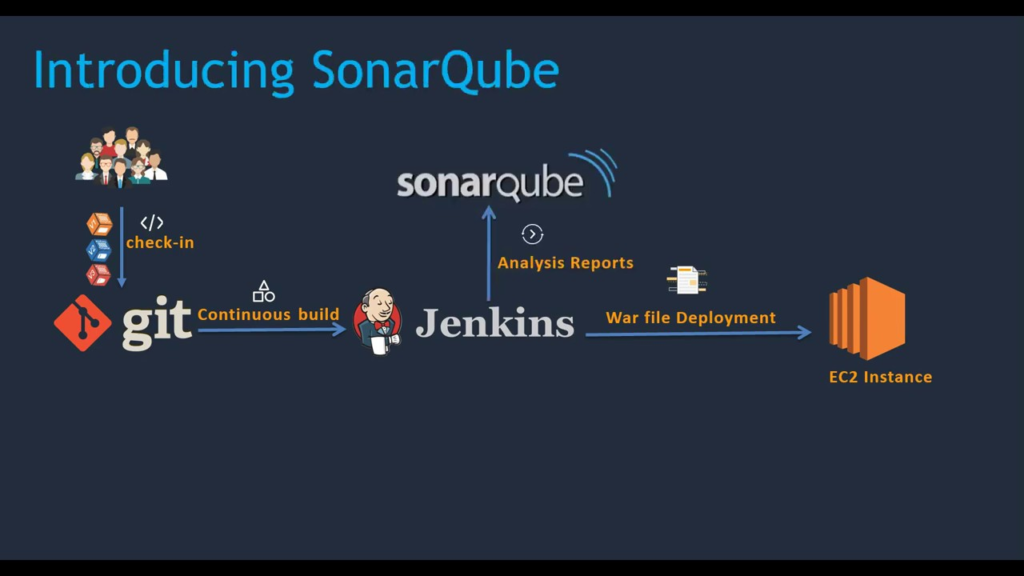
SonarQube is the leading tool for continuously inspecting the Code Quality and Security of your codebases, and guiding development teams during Code Reviews. Sonarqube is an open source tool which is use for automated code review with CI/CD Integration .
Nexus Firewall:
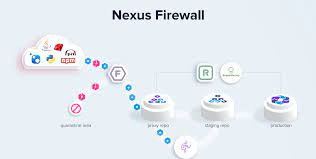
Nexus Firewall integrates automated security into the earliest stage of a DevSecOps pipeline to ensure that organizations build applications that are secure by design
Syft and Grype:
Syft:

CLI tool and library for generating a Software Bill of Materials from container images and filesystems (by anchore)
Grype:

A vulnerability scanner for container images and filesystems (by anchore)
Hope you like this blog….
- Deployment of Spring Boot Application on Kubernetes Using Helm - July 19, 2024
- Robot Framework for Selenium Automation - July 14, 2024
- Pytest Framework (Selenium Automation) - July 14, 2024

