In this guide, we’ll cover AWS IAM Create Users and Permissions, helping you understand IAM from basics to advanced setup.
AWS IAM (Identity and Access Management) is one of the most important AWS security services. It allows you to create users and permissions securely inside your AWS account. In this AWS IAM tutorial, we’ll guide you step by step — from creating users, assigning permissions, enabling MFA, to advanced IAM best practices — so you can manage access safely and efficiently.
AWS IAM controls who can do what in your AWS account. Don’t use your root account for daily work — create an admin user, give only the permissions people need, and enable MFA. These are core security steps when you set up an AWS account.
1. Introduction: What is IAM in AWS?
IAM is AWS’s service for managing access to resources. It allows you to:
- Create users (e.g., employees or applications).
- Assign permissions securely.
- Enforce security policies like MFA and least privilege. Without IAM, you’d rely on your root account, which poses significant security risks. Think of IAM as a security guard system for your AWS account.
- Related Reading: Learn how to set up your AWS account with this step-by-step guide to creating an AWS account.
👉 Think of IAM like a security guard system for your AWS account.
2. Why is IAM Important? (Beginner Level)
- Prevents misuse of your AWS account.
- Separates access for roles like developers, admins, and testers.
- Implements least privilege (only the permissions needed).
- Provides auditability through logs in AWS CloudTrail.
- Scales easily with groups and policies.
3. Key Concepts in IAM (Basic to Advanced)
🔹 Users
- Individual identity (e.g., Alice, Bob).
- Can log in to AWS Console or use CLI/SDK.
🔹 Groups
- Collection of users (e.g., Developers, Admins).
- Easier permission management (attach policy once → applies to all).
🔹 Policies
- JSON documents that define permissions.
- Types: AWS managed, Customer managed, Inline policies.
- Example: S3 read-only policy.
🔹 Roles
- Temporary credentials, not tied to a single user.
- Used for applications, EC2, Lambda, cross-account access.
- More secure than embedding access keys.
🔹 MFA (Multi-Factor Authentication)
- Extra login security step (like Google Authenticator).
- Should be mandatory for root & admins.
🔹 Identity Federation (Advanced)
- Allow users from external systems (Google, Active Directory, SAML, etc.) to access AWS.
4. AWS IAM Create Users and Permissions step by step
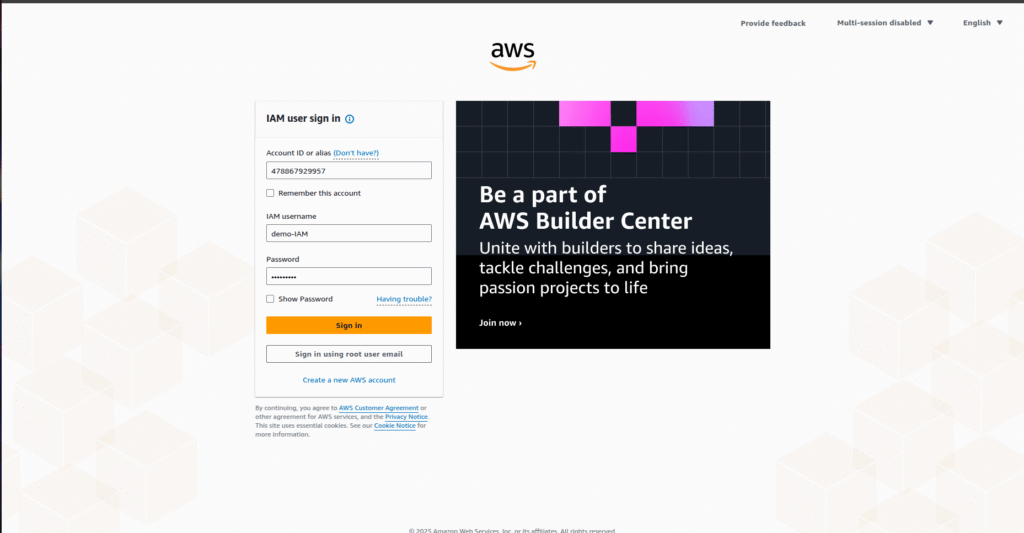
Step 1: Sign in to AWS Management Console
- Open the AWS Management Console (e.g., https://478867929957.signin.aws.amazon.com/console).
- Use your IAM username (e.g., demo-IAM) and password.
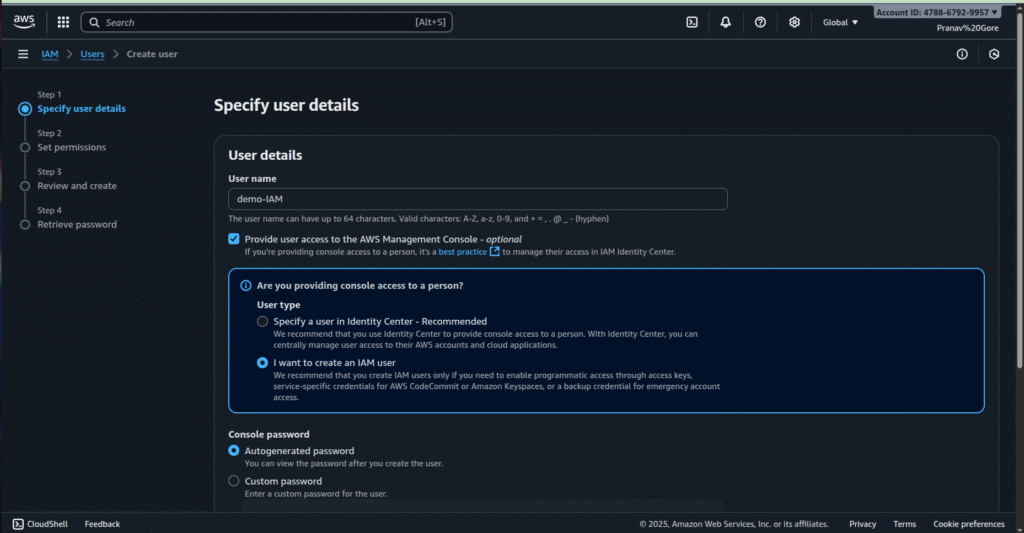
Step 2: Create a New IAM User
- Navigate to IAM > Users > Create user.
- Enter a user name (e.g., demo-IAM).
- Choose Provide user access to the AWS Management Console and select Autogenerated password or Custom password.
- Click Next: Permissions.
Specify User Details
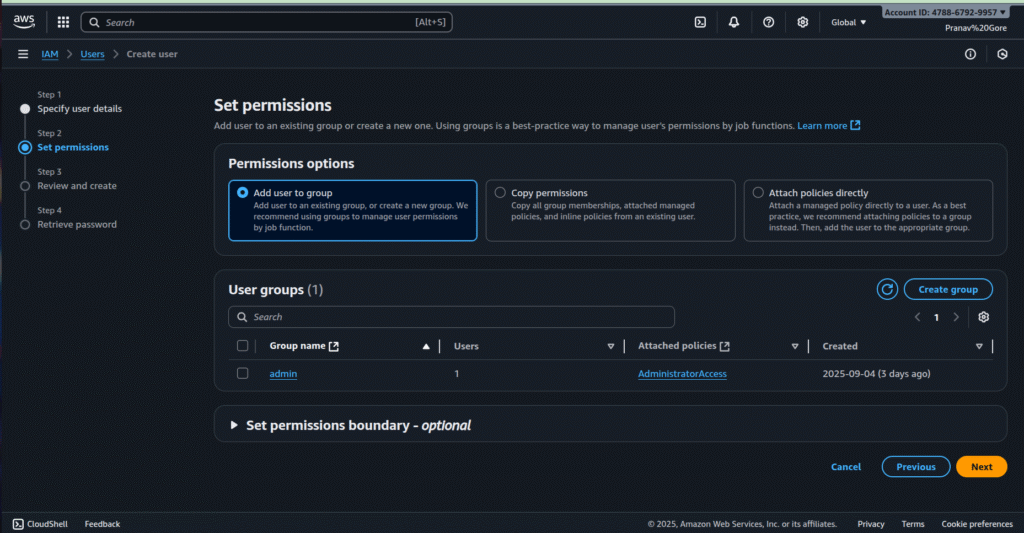
Step 3: Set Permissions
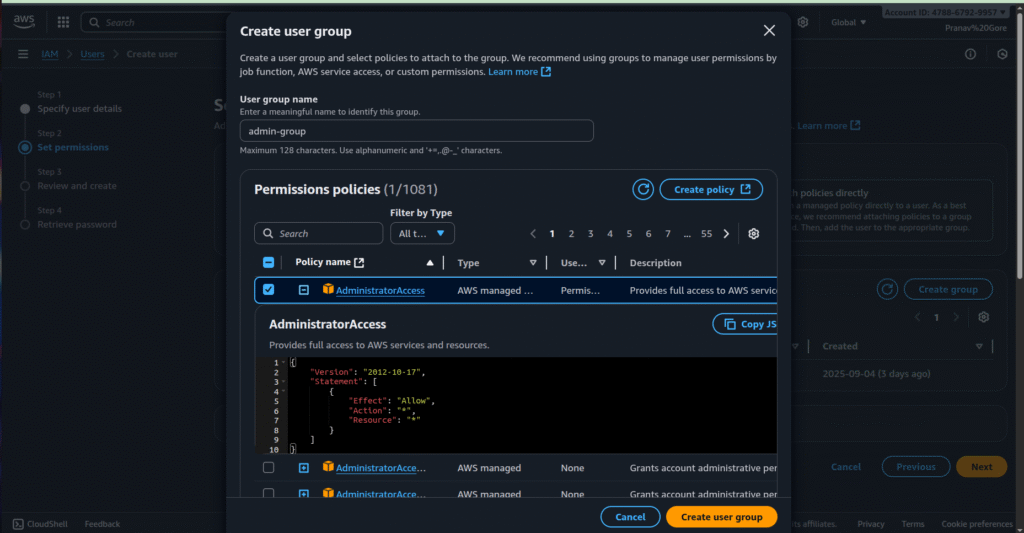
- Select Add user to group and choose or create a group (e.g., admin).
- Attach a policy like AdministratorAccess (AWS managed) for full access.
- Click Next: Tags (optional), then Next: Review.
Set Permissions
Step 4: Review and Create
- Review details and click Create user.
- Download the .csv file or email sign-in instructions to retrieve the password.
Review and Create User
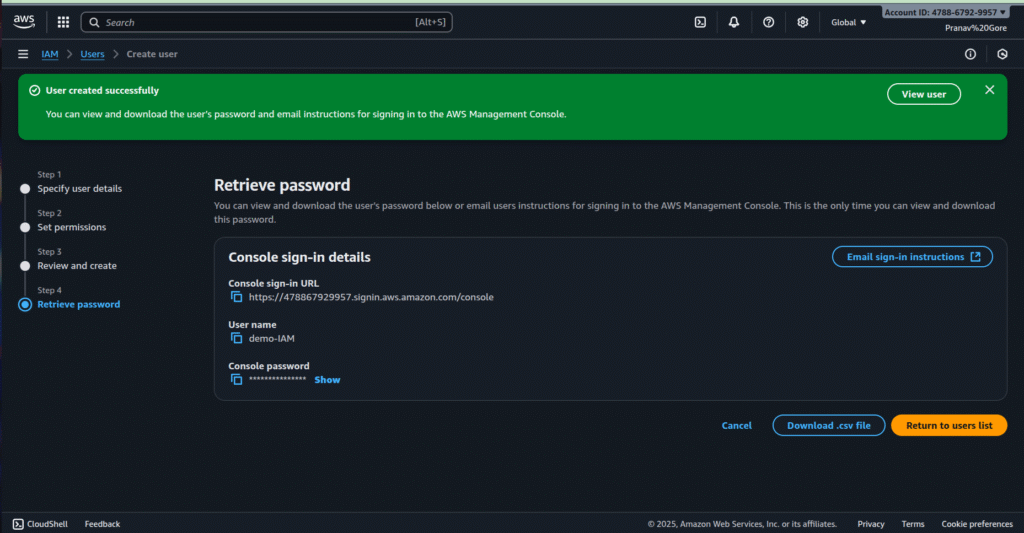
Step 5: Verify User Creation
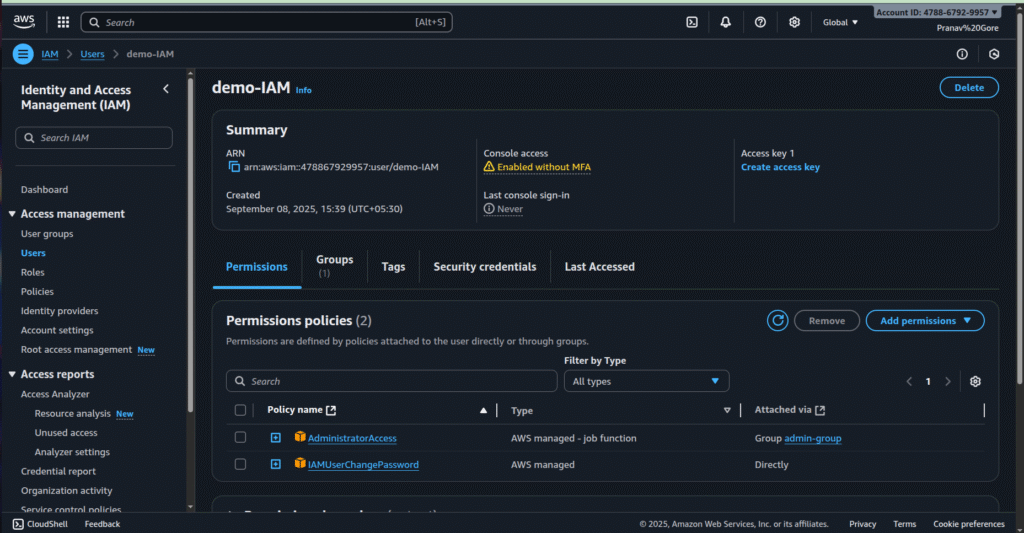
- Go to IAM > Users, find demo-IAM, and check permissions and security credentials.
- Enable MFA for added security.
User Info Screen
Now Log-in as IAM User
- JSON snippet (attach to group).
5. Advanced IAM Features
🔸 IAM Roles (for EC2, Lambda, Cross-Account)
- Instead of storing keys in code, assign a role to EC2.
- Example: An EC2 instance gets access to an S3 bucket using a role.
🔸 IAM Access Analyzer
- Helps detect overly broad permissions.
- Example: Warns if S3 bucket is publicly accessible.
🔸 Service Control Policies (SCP) with AWS Organizations
- Restrict permissions across multiple AWS accounts.
🔸 Identity Federation (SSO / External IDPs)
- Integrate with corporate login (Google Workspace, Active Directory).
🔸 Permission Boundaries (Limit Scope)
- Even admins can be restricted to specific boundaries.
6. Best Practices (Every AWS Engineer Should Follow)
✅ Never use root for daily tasks
✅ Enable MFA everywhere
✅ Follow least privilege principle
✅ Use groups & roles, not individual permissions
✅ Rotate access keys regularly
✅ Enable CloudTrail for auditing
✅ Tag IAM resources for tracking
7. Common Mistakes to Avoid
❌ Using root account for everything
❌ Attaching policies directly to users (use groups instead)
❌ Keeping old/unused access keys
❌ Not enabling MFA
❌ Using overly broad policies (AdministratorAccess everywhere)
8. Real-Life Use Cases of IAM
- Company Admins: Manage multiple accounts using roles.
- Developers: Limited S3 + EC2 access.
- Interns: Read-only permissions.
- Applications: Use IAM roles instead of access keys.
9. IAM FAQs
Q1. What is IAM in AWS?
IAM is a service to manage who can access AWS resources and what actions they can perform.
Q2. Difference between User, Group, and Role?
- User → Individual identity
- Group → Collection of users with shared policies
- Role → Temporary credentials for apps/EC2/cross-account access
Q3. How to enforce MFA?
Go to IAM > User > Security credentials > Assign MFA device → use Google Authenticator or similar app.
Q4. Can I use the root account daily?
No ❌ Only for initial setup. Use IAM admin users instead.
10. Conclusion
AWS IAM is the foundation of AWS security. By learning how to create users, assign permissions, and enable MFA, you make your AWS environment safe and scalable.
👉 Start with basics (users, groups, policies) → then adopt advanced features (roles, federation, SCPs).
📌 If you found this guide useful, share it with your team and check out more AWS tutorials.
- AI Tools for Developers: Top AI Tools Every Developer Should Know in 2026 - February 12, 2026
- What is AI? 7 Powerful and Easy Facts – Complete Beginner Guide - February 12, 2026
- How to Set Up an Okta Account – Easy & Secure Step-by-Step Guide for 2026 - January 9, 2026